13 Dec Cryptolocker Bets Big On Your Company’s Backup Integrity
By Scott R. Davis, Senior Application Engineer
If I asked you when was the last time your IT department tested your backups, would you know?
The corporate infrastructure is full of servers, years of data and potentially mandated archives of financial records or e-mails. If it vanished overnight would the company survive?
The vast majority of corporate environments backup their servers and files, but for small to medium sized enterprises that number drops. And just backing up your files is only one step, testing the backup integrity is just as essential.
This latest virus – Cryptolocker – is adding serious concern to corporate backup systems, and is a key reason to ensure backup reliability for your data.
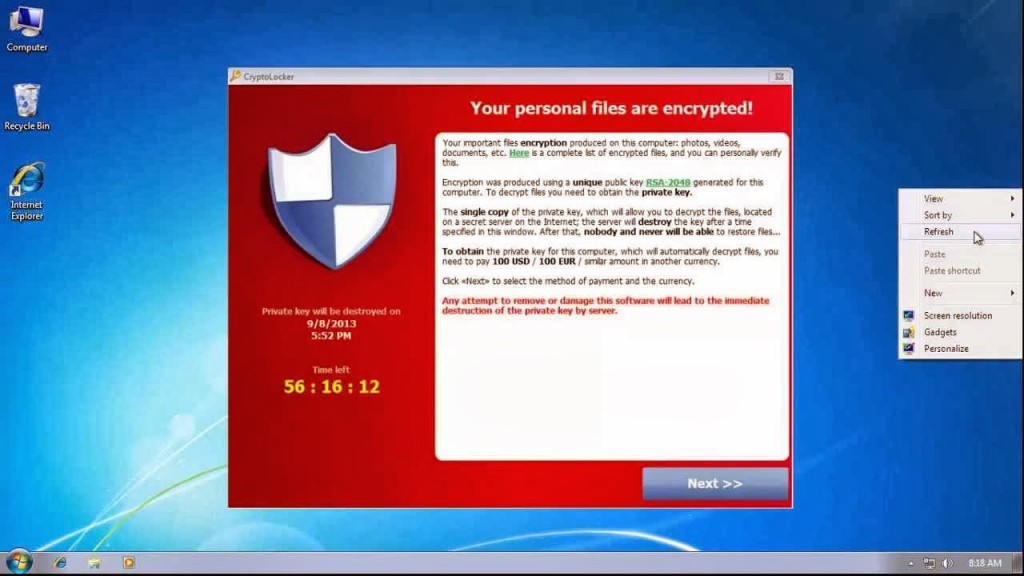
What Is The Cryptolocker Ransomware?
That virus or “ransomware” Cryptolocker is betting that your data backups are not current. Cryptolocker works by encrypting and locking files on the local hard drive and any attached networked drives. Once everything is encrypted and locked down, that workstation is greeted with a message saying that to unlock your files you will need to pay potentially hundreds of dollars for the encryption key.
In addition, it displays a countdown showing when the encryption key will be deleted, effectively deleting your data forever. Even if you do pay the ransom there is no guarantee you will regain all of your data.
Cryptolocker places a record in the Windows registry under HKEY_CURRENT_USER\Software\CryptoLocker\Files and targets the following extensions:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c
Cryptolocker first appeared back in September and is estimated to be infecting approximately 1000 computers a day in the United States and United Kingdom. Since September, the anti-virus scanning has gotten better at detecting it, but that is simply a cat and mouse game.
Cryptolocker is a nuisance and a nasty virus which when allowed onto your network leaves you little choice but to restore from backup… or pay the ransom. Even the Swansea Massachusetts Police Department has admitted to paying $750 to retrieve their data.
Our Cryptolocker Ransomware Prevention Tips
There are a few things you can do to minimize the risk of acquiring the Cryptolocker ransomware on your network.
- Back up your files. At Netrepid, we are partial to offsite solutions for data backup. Offsite solutions allow you to keep your data safe, secure, and available should ANYTHING go wrong at your current business location – cyber or physical.
- Educate your end users. Cryptolocker is typically delivered as an e-mail zip file that once run begins to encrypt and lock.
- Keep OS and softwares up to date. Make sure your users devices have the latest operating systems and updates are installed.
- Utilize antivirus solutions. Maintain current and updated anti-virus protection on your servers and workstations.
I would also recommend creating a software restriction policy to block executable files from running in the specific user-space areas that Cryptolocker uses to launch itself.
For more information on setting up a software restriction policy, Computerworld has a great guide here.
Cryptolocker is betting big that your company backups are missing that key piece or haven’t been tested and fail. You don’t want to be on the losing end of that bet.



